Information Security
Security Management Services | Digital Risk Protection – Cyberint Argos | Breach and Attack Simulation – KEYSIGHT Threat Simulator | AI cyber security defense – Darktrace | System Vulnerability Scan Service | Webpage Vulnerability Scan Service | Penetration Testing | Source Code Inspection Service | IOT/OT asset discovery, vulnerability management, and threat detection | ISMS and PIMS Services | Social Engineering | OIS- ISMS、PIMS, and GHG Emission Reporting services
Source Code Inspection Service
Brief Introduction
Hackers often use program development loopholes or vulnerabilities to perform attacks and steal data; therefore, the challenges of information security management during program development or for the maintainers when the software development cycle schedule is tight also increase. Through the source code inspection service, vulnerabilities of program codes are analyzed quickly and comprehensively in order to discover potential risks. Repairing loopholes in program codes can effectively improve the quality of the application’s security.
Descriptions of Features and Advantages
The original program codes are inspected for source code inspection to search for and identify potential security vulnerabilities in the program and to analyze information such as the vulnerability type and the attack route; developers can modify the program according to the analysis results to prevent vulnerabilities from being generated. The execution of source code inspection is suitable when the system is either in the development or maintenance stages.
Benefits
- Improve program security: Find the security vulnerabilities and flaws in the program code through source code inspection to improve the security of the application and the stability of the program’s performance.
- Complete analysis: Complete source code inspection coverage can ensure that all program execution paths can be analyzed effectively.
- Clear results: Clearly identify where the vulnerabilities occurred and their operation paths to find the most effective correction method.
- Prevent online systems from being affected: Actual inspection is not performed for online systems; therefore, there will be no impact to online systems. Avoid affecting services and user rights during the inspection process.
- Reduce manpower and tool costs for enterprises: There is no need to spend a large budget to purchase inspection tools and configure dedicated manpower.
Applications
Agencies, financial units, web service providers of enterprises, and web application developers where the Cyber Security Management Act apply
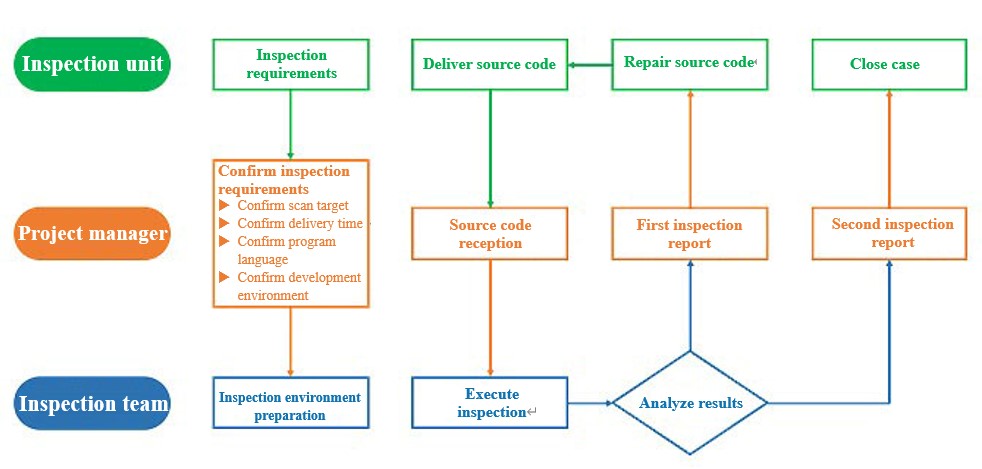
Service Process
Contact Window
Understand Other Related Testing Services
System vulnerability Scan Service Webpage Vulnerability Scan Service
Announcement
In May 2023, Open Information Security (OIS), a cybersecurity subsidiary, was established by the original HwaCom Systems Inc cybersecurity team. With its business operations now independent, Open Information Security is committed to providing customers with professional cybersecurity expertise, high-quality services, and a sustainable business approach.

