Information Security
Security Management Services | Digital Risk Protection – Cyberint Argos | Breach and Attack Simulation – KEYSIGHT Threat Simulator | AI cyber security defense – Darktrace | System Vulnerability Scan Service | Webpage Vulnerability Scan Service | Penetration Testing | Source Code Inspection Service | IOT/OT asset discovery, vulnerability management, and threat detection | ISMS and PIMS Services | Social Engineering | OIS- ISMS、PIMS, and GHG Emission Reporting services
Penetration Testing
Brief Introduction
Penetration testing is to simulate the attack method of the real hackers, to test the security strength of the target host or network service, comprehensively explore potential security problems through professional security detection technology, put forward suggestions for improvement, and provide re-testing operations after the security vulnerability is corrected to confirm the effectiveness of vulnerability risk patching to strengthen the information security policy.
Descriptions of Features and Advantages
Penetration testing is attacks that mimic the real online world, and the performers use common detection tools and professional techniques to collect and analyze the information obtained according to the data collection, formulate penetration methods and strategies, and use manual methods to bypass the system or network service to discover exploitable weaknesses and vulnerabilities, then try to obtain unauthorized access permissions, and launch actual attacks on the systems and networks.
Benefits
Professional testing team
The testing team has many international security certificates, rich experience in security, and carries out penetration testing planning and decision-making application according to the information obtained by data collection and analysis.
Standardized operating procedures
Fast and effective service qualities are provided by following the international testing operation standards OSSTMM, OWASP, and the standardized testing operating procedures they prescribed.
Professional vulnerabilities Analysis and Recommendations
Analysis reports are provided for different aspects of the execution results to explain the vulnerabilities found and the risks that may be caused, and put forward relevant repair suggestions.
Customized test planning and risk assessment
Requirement interviews are conducted before testing to confirm the test situation and make risk assessment recommendations to prevent unexpected data damage or loss, then test plans are formulated to create the best test plan.
Expert consulting
Professional vulnerabilities repair consultation with quick response and feedback to provide effective solutions and assessments, and strengthen security protection.
Applications
The Cyber Security Management Act applies to government agencies, financial units, enterprises, and enterprise website service providers.
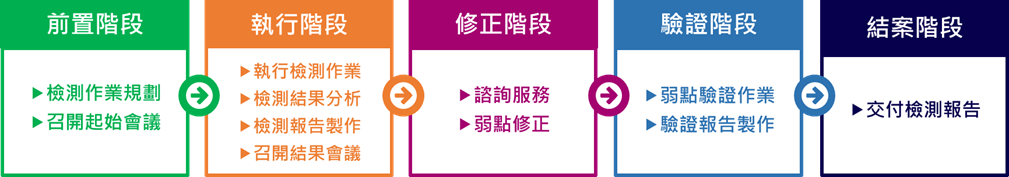
Service Process
.
Tools
Performers are supplemented by commonly used detection tools, such as vulnerability scanning tools or other tools such as Burp Suite, Metasploit, Nmap, Kail Linux and others, combined with rich security experience and detection technology to manually conduct penetration testing and inspection.
Contact Window
Understand Other Related Testing Services
System Vulnerability Scan Service Webpage Vulnerability Scan Service
Source Code Inspection Service
Announcement
In May 2023, Open Information Security (OIS), a cybersecurity subsidiary, was established by the original HwaCom Systems Inc cybersecurity team. With its business operations now independent, Open Information Security is committed to providing customers with professional cybersecurity expertise, high-quality services, and a sustainable business approach.

