Information Security
Security Management Services | Digital Risk Protection – Cyberint Argos | Breach and Attack Simulation – KEYSIGHT Threat Simulator | AI cyber security defense – Darktrace | System Vulnerability Scan Service | Webpage Vulnerability Scan Service | Penetration Testing | Source Code Inspection Service | IOT/OT asset discovery, vulnerability management, and threat detection | ISMS and PIMS Services | Social Engineering | OIS- ISMS、PIMS, and GHG Emission Reporting services
Social Engineering
Brief Introduction
Social Engineering refers to the manipulation of human psychology, such as curiosity, fear, and greed, to deceive individuals into performing actions that lead to the theft of sensitive information. This is often done through emails, text messages, social media, and other forms of communication. Due to its low barrier to entry and the ability to send messages in large volumes, it often becomes a security vulnerability, causing significant losses. To reduce information security risks and enhance personnel awareness of social engineering, the Social Engineering Service simulates the sending of fake attack emails to recipients. This helps understand user behavior and information security awareness. By analyzing the results of these exercises, potential security gaps can be identified, and internal training can be implemented to strengthen overall information security awareness.
Descriptions of Features and Advantages
The service involves conducting social engineering on various email accounts. Following standardized operating procedures, design different types of exercise email templates. Using email simulation tools, these emails are sent to the target recipients at agreed times and in different combinations. Based on user behavior responses, the results are analyzed to determine the success rate and distribution of the phishing emails. Provide improvement suggestions as a basis for information security management.
Benefits
- Enhancing Overall information security Awareness: Through Social Engineering, participants become aware of the existence of social engineering and increase their vigilance. Internal training measures help cultivate basic information security knowledge among participants, effectively reducing the risk and loss from social engineering attacks.
- Professional Testing Team: The testing team has several international information security certifications, and has rich experience in information security, able to grasp vulnerability problems effectively.
- Standardized operating procedures: Quick and effective service quality is provided by following the standardized testing operating procedures set.
- Professional vulnerability analysis and recommendations: Different aspects of user behavior analysis reports are provided, then complete and feasible repair recommendations are proposed according to the vulnerabilities discovered.
- Customized test plans: Requirement interviews are performed before testing to understand personnel attributes, design customized email templates, and formulate testing plans to create the best testing solution.
Applications
Agencies, financial units, and enterprises where the Cyber Security Management Act can be applied.
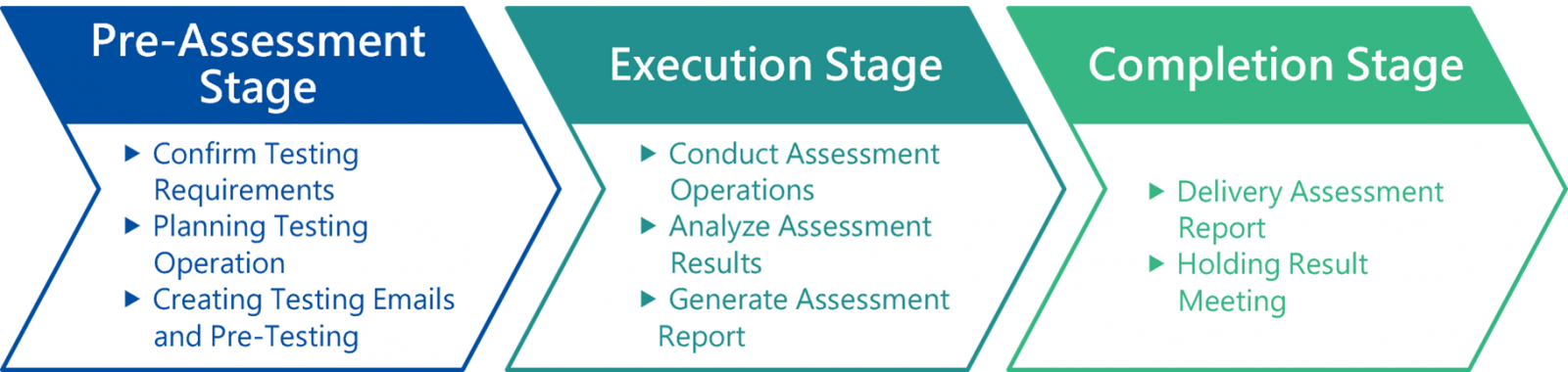
Service Process
Contact Window
Announcement
In May 2023, Open Information Security (OIS), a cybersecurity subsidiary, was established by the original HwaCom Systems Inc cybersecurity team. With its business operations now independent, Open Information Security is committed to providing customers with professional cybersecurity expertise, high-quality services, and a sustainable business approach.

