Information Security
Security Management Services | Digital Risk Protection – Cyberint Argos | Breach and Attack Simulation – KEYSIGHT Threat Simulator | AI cyber security defense – Darktrace | System Vulnerability Scan Service | Webpage Vulnerability Scan Service | Penetration Testing | Source Code Inspection Service | IOT/OT asset discovery, vulnerability management, and threat detection | ISMS and PIMS Services | Social Engineering | OIS- ISMS、PIMS, and GHG Emission Reporting services
Webpage Vulnerability Scan Service
Brief Introduction
Network environments and network activities are becoming more and more diverse. Many known vulnerabilities have high-risk loophole threats due to problems such as improper website configuration settings, encrypted connection settings or security settings by enterprises, and may give hackers opportunities for attacks. In order to reduce information security risks and fully understand and grasp the security vulnerabilities that exist for websites, a website vulnerability scan service is used to scan target websites, and information security experts will perform professional analyses, then propose effective and feasible improvement plans to strengthen and patch the vulnerabilities. After the vulnerabilities are corrected, they will be tested again for verification. Comparative analysis will be performed to discover security vulnerabilities and repair them effectively in time, reduce the chance of being attacked significantly, and avoid the risk of the enterprise being intruded.
Descriptions of Features and Advantages
A security vulnerability scan is performed on the various target websites. Vulnerability scan tools are used together with other commonly used tools and instructions according to standardized operating procedures to scan the various web applications to check whether security vulnerabilities exist. Effective and feasible repair recommendations can be proposed by checking and comparing the information and performing professional analysis. After the vulnerabilities of enterprises are repaired, they are re-tested for verification to confirm the effectiveness of the vulnerability repairs to reduce information security risks.
Benefits
- Professional testing team: The testing team has several international information security certifications, and has rich experience in information security, able to grasp vulnerability problems effectively.
- Standardized operating procedures: Quick and effective service quality is provided by following the standardized testing operating procedures set.
- Professional vulnerability analysis and recommendations: Different aspects of statistical data analysis reports are provided, then complete and feasible repair recommendations are proposed according to the vulnerabilities discovered.
- Customized test plans: Requirement interviews are performed before testing to formulate testing plans and create the best testing solution.
- Expert consultation: Professional vulnerability repair consultation with quick responses and feedback provides effective solutions and evaluations as the basis for management.
Applications
Agencies, financial units, enterprises, web service providers of enterprises, and web application developers where the Cyber Security Management Act can be applied.
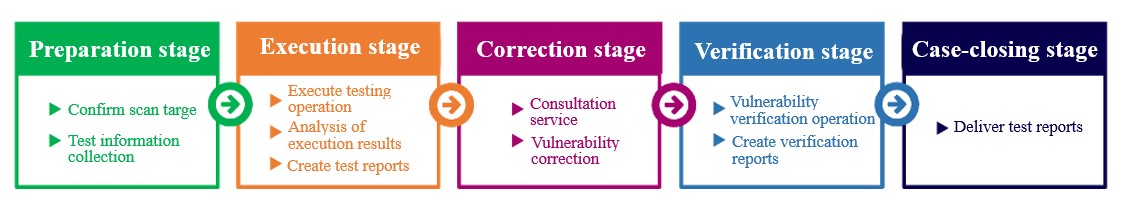
Service Process
Contact Window
Understand Other Related Testing Services
System Vulnerability Scan Service Penetration Testing
Source Code Inspection Service
Announcement
In May 2023, Open Information Security (OIS), a cybersecurity subsidiary, was established by the original HwaCom Systems Inc cybersecurity team. With its business operations now independent, Open Information Security is committed to providing customers with professional cybersecurity expertise, high-quality services, and a sustainable business approach.

